Your next breach likely won’t come from your code. It will emerge from one of your 500+ dependencies, external contributors, or forgotten build systems.
Modern software development relies on hundreds of third party components. Between open-source packages, third-party libraries, external APIs, offshore contractors, and cloud infrastructure, today’s applications rely on an entire software supply chain that extends far beyond your direct control. Each component is a potential backdoor. Your attack surface now includes every npm install, every contractor commit, every CI/CD workflow.
This article cuts through the noise with practical strategies for building a secure software supply chain across three critical areas: managing external dependencies, securing distributed teams, and vetting development partners. No frameworks, no buzzwords – just what actually works for engineering teams under pressure to ship.
Understanding Supply Chain Risk
Modern deployment pipelines lean heavily on outside code—open-source components, libraries, cloud services, and contributions from remote teams or vendors. Each dependency speeds development yet widens the attack surface.
Before choosing tools or defenses, engineering leaders need a clear map of where risks enter the pipeline, how they propagate across environments, and which controls stop them from spreading.
What is software supply chain security?
Supply chain security involves protecting all the interconnected systems and components that facilitate secure delivery, from contributor access to third-party packages, security tools, and secrets detection.
Common weak points and security risks include:
- Malicious or compromised open-source packages (typosquatting and dependency confusion)
- Hardcoded or leaked credentials in code and CI/CD systems
- Excessively broad repository permissions and inadequate contributor vetting
- Unverified build artifacts or absent signing protocols
- Insider threats within distributed or external teams
Securing the software supply chain requires continuous monitoring with Software Composition Analysis (SCA) tools , robust threat intelligence, provenance controls, and visibility across environments and partners—key principles emphasized in CISA’s Developer Guide to Securing the Software Supply Chain.
As development cycles get shorter and delivery expectations rise, teams are increasingly turning to third-party code and globally distributed teams. Nearshoring and outsourcing promise speed and scalability, but without effective governance, they also amplify risk.
Recent data breaches highlight the reality of these risks and the emerging threats they present :
- SolarWinds: attackers compromised a trusted software update, spreading malware downstream to thousands of customers
- Log4Shell: a vulnerability in a widely used library exposed systems across the globe
- Codecov: a malicious script alteration leaked credentials and tokens from CI/CD pipelines for months
Software supply chain security has become a strategic concern that directly affects delivery.
When External Teams Become Attack Vectors
Working with distributed teams and outsourcing partners speeds up delivery, but it also expands your attack surface in ways that catch many organizations off guard.
The problems start small. Maybe a contractor in Eastern Europe commits a package with an outdated dependency. A team in Latin America shares AWS keys through Slack because the IAM setup is taking too long. Your vendor’s Jenkins instance runs on ancient plugins because nobody owns the upgrade cycle. Before you know it, you’re debugging a production incident that traces back to source code you’ve never seen, written by people you’ve never met.
The usual suspects:
- Dependencies that haven’t been updated since 2019
- API keys hardcoded in config files
- Shared GitHub accounts that bypass security protocols
- Zero visibility into how your partners actually build and test code
Here’s the thing most security frameworks miss: geography doesn’t matter, but process discipline does. Whether your team sits in San Francisco or São Paulo, they need the same tooling, the same access controls, and the same audit trail. No exceptions, no “we’ll fix it next quarter.”
Where Your Supply Chain Actually Breaks
Remember when dependencies were just a ‘package.json’ problem? Those days are gone. Now every Docker base image and GitHub Action you copy-paste offers a potential backdoor into your infrastructure. The same tools and supply chains that let us ship faster have turned into our biggest liabilities.
Your attack surface isn’t just your code anymore. It’s the CI runner your contractor spun up last month. It’s the service account with admin rights that “temporarily” got created two years ago.
The Dependency Nightmare Nobody Talks About
Most teams grab that React component or Python package without thinking twice. It has 10,000 GitHub stars, so it must be fine, right?
Here’s what actually happens: A single import pulls in three more packages, untouched since 2018. Your security team discovers the compromise six months later, after multiple production deployments.
The typosquatting game has gotten sophisticated too. Think ‘python-dateutil’ versus ‘python-dateutils’, or ‘node-sass’ versus ‘node-sass-official’. One character difference, and suddenly you’re mining crypto.
And transitive dependencies? Most teams lack visibility into what’s actually running in production. You think you’re using 50 packages, but your dependency tree shows hundreds.
The worst part? We treat external code differently than internal code. That random npm package gets waved through, but your PR needs three approvals.
CI/CD and Build Pipeline Weaknesses
Build systems are prime real estate for malicious code because they touch everything. Your Jenkins instance has write access to prod. Your GitHub Actions can read every secret. Every step of your build process leaves traces. Smart attackers know this and target the weakest points – usually the handoffs between stages.
The defaults will burn you. Cloud continuous integration runners log everything, including your API keys. Service accounts get created with admin rights because someone needed to debug something once. Nobody signs artifacts because “we trust our pipeline.” Then one day your build server starts shipping binaries with a little something extra.
Distributed teams make this worse. That contractor who left six months ago? Their credentials still work. The script they wrote to “temporarily” bypass approval gates? Still running, letting attackers gain unauthorized access. Every compromise cascades because build systems intentionally have broad access. SLSA and similar frameworks push for verifiable builds and isolated environments, but most teams are nowhere close to implementing them.
Source Code Integrity Gaps
Code repositories are often configured like it’s still 2015. Branch protection rules that aren’t enforced. Developers with admin access who shouldn’t have it. Secrets scattered across config files because someone needed to ship fast.
External contributors and third party vendors amplify every weakness. Shared accounts persist because onboarding is painful. Reviews get rubber-stamped because deadlines loom. Your partners might not even use two-factor authentication, let alone signed commits or proper access controls.
When someone rewrites history on your main branch, you lose weeks of work. When credentials leak, you’re rotating keys at 3 AM. When tampering goes undetected, you ship vulnerable code to customers. The damage compounds fast.
Common vs. Best-in-Class Supply Chain Practices
Most teams know their supply chain security isn’t great. The hard part is figuring out what “good” actually looks like and where to focus first.
Here’s how typical setups compare to what high-performing teams actually do:
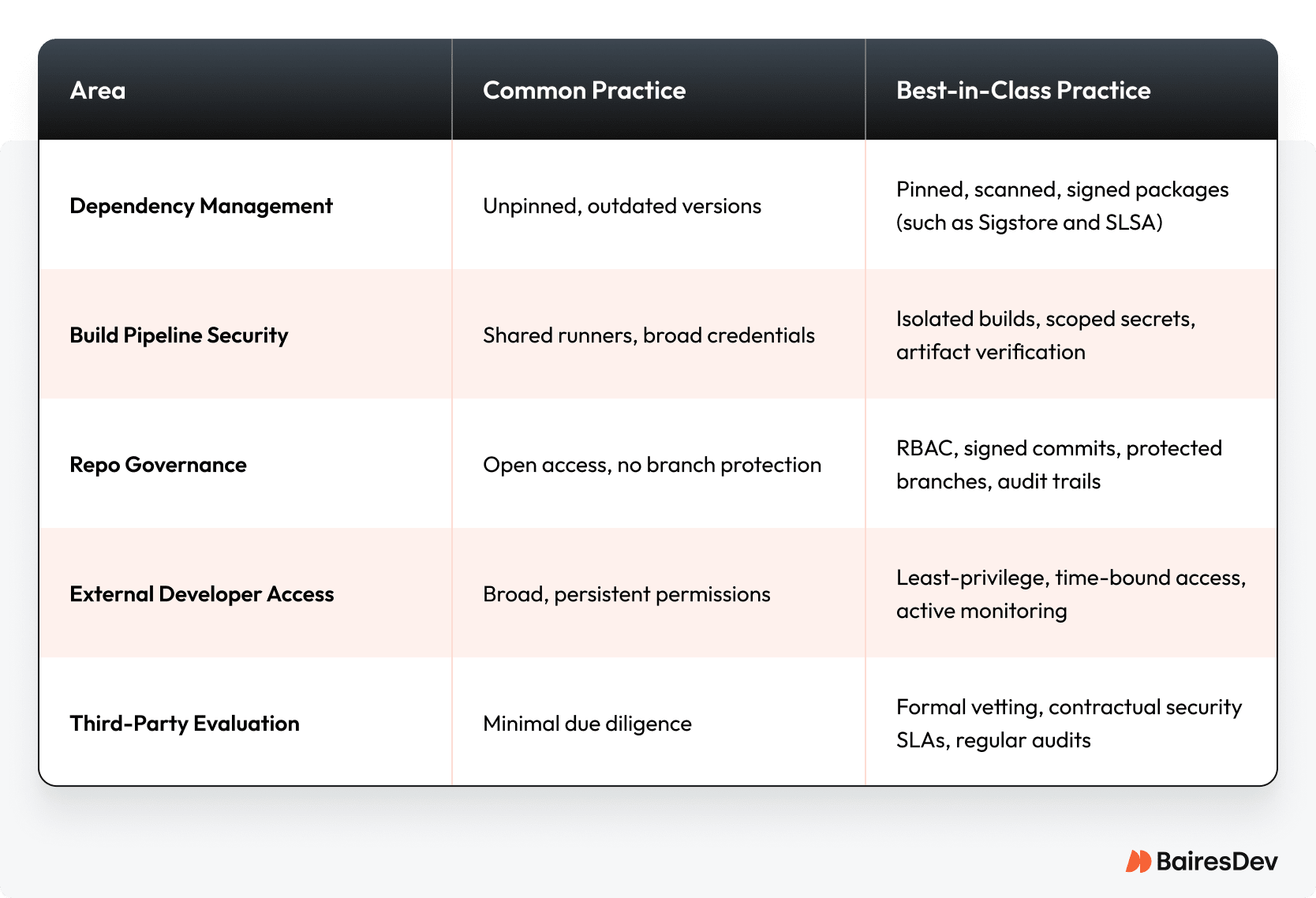
The gap between these columns is where breaches happen. Pick your weakest area and start there.
Getting Your Supply Chain Security Right
Stop treating security as a check-the-box exercise or something you bolt on after the fact. Here’s what actually works, organized by impact and ease of implementation.
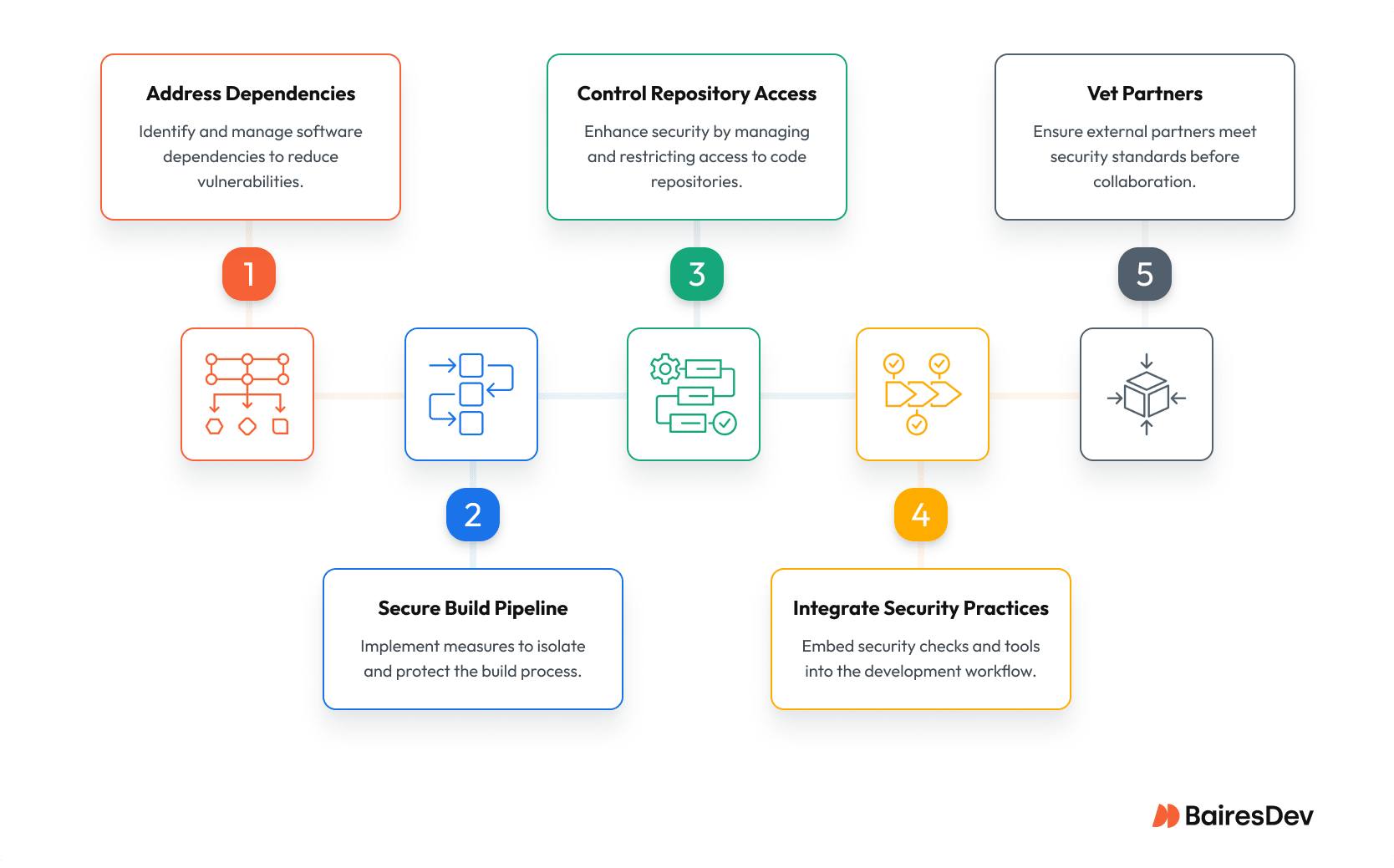
Start with Dependencies (Highest Impact, Easiest to Fix)
- Generate a software bill of materials (SBOM) for every service
- Pin your versions – “latest” is not a version strategy
- Actually verify signatures when they exist
- Set up automated alerts for your dependency tree – obscure libraries often become liabilities
Lock Down Your Build Pipeline
- Isolate build environments – shared runners are shared risk
- Scope secrets to exactly what they need – your test runner doesn’t need prod access
- Sign everything you ship and verify everything you pull
- Keep immutable logs of every build – you’ll need them when something goes wrong
- Review your pipeline config monthly – drift happens fast
Fix Repository Access
- Enable 2FA everywhere – no exceptions for senior engineers
- Use branch protection that actually protects – requiring reviews means nothing if anyone can approve
- Automate access removal – people leave, permissions should too
- Set up alerts for force pushes and permission changes
Make Security Part of How You Work
- Run security checks in pre-commit hooks, not after merge
- Make security tools as fast as your unit tests
- Give everyone visibility into the same dashboards
Vet Your Partners Before They Touch Code
- Ask for their SBOM practices upfront – if they don’t know what that is, look elsewhere
- Verify they can integrate with your toolchain before signing contracts
- Check their build logs and commit history – past behavior predicts future behavior
Managing Risk When Your Code is Everywhere
Start with an honest risk assessment. Not the checkbox kind for compliance, but the kind where you actually trace what could go wrong. Most teams have no idea who can access what, which dependencies are actually critical, or how a breach in one system would cascade through others. Here’s how to fix that.
Know Your Actual Attack Surface
Start by mapping who touches your code. Not just your employees – every contractor, every service account, every automated system. Document which teams own which services and what dependencies they pull in.
This isn’t busywork. Last year, we discovered a departed contractor’s GitHub token was still deploying to production through a forgotten Jenkins job. That token had access to 47 repositories. Nobody knew until we mapped it.
Understand Your Blast Radius
When credentials leak, how far does the damage spread? Most organizations reuse secrets across projects because it’s convenient. Your staging database password is probably your production password with “-staging” appended. Your CI/CD tokens likely have permissions they haven’t needed since 2021.
Run this exercise: Pick any service account and trace what it can access. Include transitive permissions – what can it reach through other systems? The results are sobering.
Model Threats That Actually Matter
Skip the academic frameworks. Focus on three scenarios:
- A malicious package gets into your dependency tree
- An attacker compromises your build system
- A trusted partner’s credentials get stolen
For each one, trace the kill chain. Where would you detect it? How would you stop it? Most teams discover they wouldn’t detect anything until customers complain.
Get Everyone on the Same Page
Security, engineering, and procurement need to agree on basics: How do you evaluate vendors? What access is acceptable? Who’s responsible when external code breaks?
Write it down. Make it enforceable. Update it when you learn something new.
Tools That Actually Help
SLSA and in-toto aren’t just buzzwords – they solve real problems. They create audit trails that prove your code hasn’t been tampered with between commit and deploy. Combined with SBOMs, you can finally answer “what’s actually running in production?” with confidence.
Picking Partners That Won’t Burn You
Good vendors do security better than most internal teams. They must – it’s their business model. The trick is identifying which ones actually deliver versus just talk about it.
Focus on four things:
- Access control: Scoped credentials from day one, not “we’ll fix permissions later”
- Tool compatibility: They should work with your SBOM and signing requirements, not around them
- Audit trails: Every commit, every build, every deployment should be traceable
- Actual alignment: They follow your security standards, not their interpretation of them
Partner Security Checklist
Don’t take their word for it. Verify:
- SBOMs for everything – including dependencies of dependencies
- Signed builds – if they can’t prove it wasn’t tampered with, assume it was
- Scoped access – nobody needs admin rights to everything
- Isolated environments – dev mistakes shouldn’t hit prod
- Standards compliance – NIST/OWASP/SLSA aren’t optional
- Automated credential rotation – manual processes always fail
- Real-time logs – not “we’ll send you a report next week”
- Clear responsibilities – who owns incident response?
Partners who can’t check these boxes will cost you more than they save. More importantly, they’ll weaken your entire security posture.
Transform Supply Chain Security Into A Competitive Advantage
Your supply chain is probably already compromised. The question is whether you know about it and what you’re doing about it.
Every unpatched dependency, every overprivileged service account, every partner with weak practices is a ticking time bomb. The companies that survive the next SolarWinds-scale attack won’t be the ones with perfect security – they’ll be the ones who can detect, contain, and recover fast.
Stop treating software supply chain management as a compliance checkbox. The teams winning in this space use security constraints to ship faster, not slower. They catch issues in minutes instead of months. They trust their partners because they verify everything.
You already know what needs fixing. The question is whether you’ll do it before or after your next incident.
Frequently Asked Questions
What’s the biggest software supply chain risk when outsourcing development?
The top risk is insufficient control over external contributors, especially when it comes to unmanaged access, weak CI/CD practices, and unverified code changes. Without clear governance, a trusted vendor can become an unexpected attack vector, leading to various security risks .
How can you ensure that a development partner follows secure coding and delivery practices?
Require signed builds, SBOMs, and integration into your CI/CD toolchain. Establish a formal onboarding checklist, enforce scoped access, and schedule regular audits not just for compliance, but also for security controls, code quality, and operational discipline.
What frameworks or standards should you expect vendors to comply with?
Look for alignment with SLSA (Supply-chain Levels for Software Artifacts), OWASP Secure Software Contract Annex, and NIST 800-218 (SSDF). These frameworks set clear expectations for build provenance, credential management, and artifact verification.
What are signs that your current vendor may be introducing unnecessary risk?
Lack of build traceability, persistent over-permissions, no signed artifacts, or delayed responses to access change requests are red flags indicating potential exposure to known vulnerabilities . So is any reluctance to share code review practices or integrate with your toolchain.
How can you monitor risk across a globally distributed team or multi-vendor environment?
Start by mapping access and code ownership across all teams and vendors. Without this visibility, software supply chain attacks can propagate undetected for months. Require comprehensive audit logs from every partner and implement automated anomaly detection in your CI/CD workflows. The goal is to spot unusual patterns before attackers can pivot through your systems.
How often should you audit external code and access?
Perform codebase and access audits quarterly at minimum, and after any personnel change. Incorporate vendor audits and adequate security measures into your broader DevSecOps or compliance review cycles.







