Open source software has become a foundational part of modern enterprise software stacks. It’s a global free software movement, and nearly every application today includes hundreds of open-source components.
Whether or not you’re invested in it, chances are your business already runs on open-source, at least to some extent. The real question is: are you using it strategically?
The future of open source will be defined by how well it integrates into complex, regulated environments. For enterprises, that means treating OSS as a disciplined part of the software development process, with the right tooling, governance, and long-term support in place.
The Ubiquity of Open Source Software in 2026
The 2025 Open Source Security and Risk Analysis (OSSRA) report shows that open source is everywhere. Approximately 97% of commercial codebases incorporate some form of open-source code.
70% of the code scanned originates from open-source sources. The average application today includes more than 900 open-source components.
Open source software projects now shape the pace and direction of software development across nearly every industry, accelerating innovation and reducing time to market.
Open Source: The Catalyst for Rapid Development
Open source software was originally viewed as a phenomenon driven by ideals. It was about freedom and transparency; developers shared software and ideas, encouraging other community members to contribute to projects they felt passionate about. Today, it’s become a practical tool for getting things done faster and smarter.
This free software movement enables faster execution by reducing duplication. Teams no longer start from scratch. Open source often covers 70% of the foundational work, allowing engineers to focus on what’s unique to their project. This is what you gain by integrating well-supported OSS libraries for core functions such as authentication, serialization, and messaging.
Whether you realize it or not, your business likely relies on open source solutions, even within proprietary software systems you use every day.
Organizations that fail to use open source strategically are missing out on faster software development cycles, more transparent security, and major cost savings.
Why Security Policies Matter
Is open source secure? It can be, provided it is managed correctly.
Open source software offers flexibility and speed, but it also brings shared responsibility. Anyone can access the code, including bad actors. That makes governance essential.
Every enterprise using open-source solutions should have a clear policy in place. At a minimum, it should cover:
- Regular vulnerability scans
- Software composition analysis (SCA)
- Timely patching
- Approved license types (GNU General Public License, Apache license, etc.)
Aligning your policy with frameworks like ISO 27001 or NIST ensures your OSS usage holds up in audits and meets all compliance requirements.
Software Development and Licensing
Licensing is one of the most important aspects of open source software in a commercial setting.
Every open-source project includes a license that governs usage. Some are flexible, others impose strict conditions, especially around sharing derivative work.
Open-source software licenses aren’t just check-the-box affairs. They set the terms for how software can be used, shared, and supported in a commercial setting.
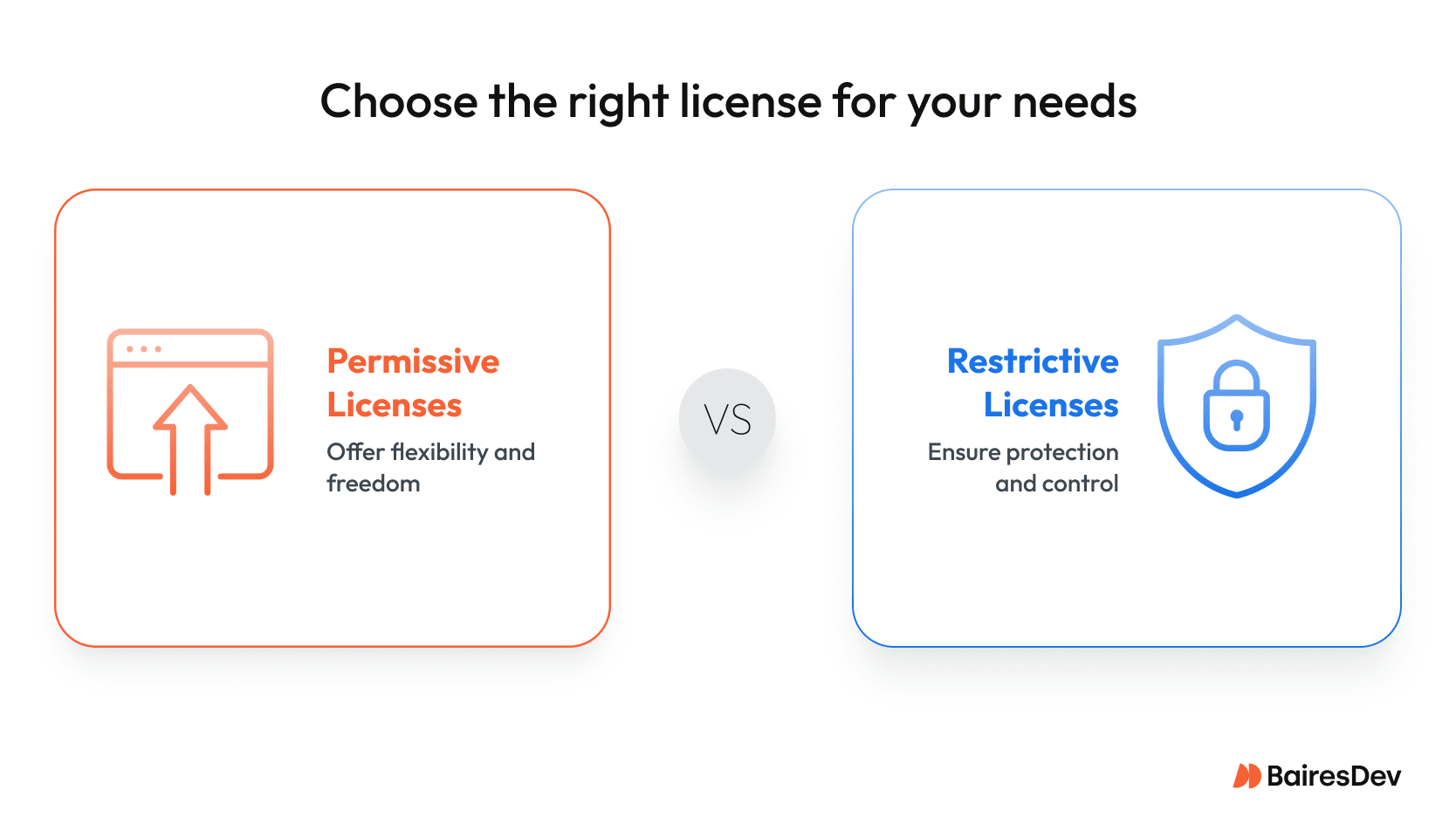
Key Licence Types:
- MIT – Highly permissive and flexible. Allows broad use with attribution, including in proprietary software.
- Apache 2.0 – Similar to MIT, with added patent protections. A strong choice for commercial software vendors.
- GPL – Restrictive, copyleft license. Requires that derivative works be open-sourced, limiting commercial flexibility.
The MIT license is essentially a permissive license, while the GPL is a protective license. The GPL ensures that derivative works remain free, while the MIT license allows proprietary derivatives. Apache 2.0 is widely considered the most business‑friendly open source license.
Choosing the wrong license can introduce legal or support headaches and limit how you bring products to market. The right license can offer flexibility, scale, and long-term control.
OSS Communities Support Long-Term Viability
One of the most strategic, yet often overlooked, advantages of open-source software is the strength of its global community.
Behind every great open source project is a group of people who dedicate their time to bug fixing, contributing new code, creating documentation, and supporting each other. Open-source communities aren’t just technical support forums; they’re ecosystems of shared knowledge with diverse perspectives. Most are not transactional, but driven by enthusiasm.
Being part of that community — even just as a user — gives you access to a global network of developers, best practices, and ready-made solutions. And if your team contributes back, you’re building a reputation, exerting influence, and getting goodwill in return. This strengthens your team’s standing within the developer community.
For engineering leaders, these communities also offer indirect access to highly skilled talent: developers who’ve already demonstrated real-world capability through public contributions.
Talent Strategy: Why OSS Experience Is a Competitive Advantage
For developers, open-source projects offer a hands-on way to grow. The code is out in the open, so they can dive in, experiment, and learn by doing. These projects are a chance to get feedback from more experienced programmers and become part of a larger developer community. For many developers, open source communities also provide a chance to network, build a reputation, and further their careers.
Today’s top engineers expect to work with modern, open-source tooling: Kubernetes, Terraform, Docker, and Git-based workflows. Supporting OSS contributions can improve morale, strengthen your tech brand, and make your roles more attractive to senior talent.
A Strategic Benefit for Modern Business
Open- or closed-source? Each model has its trade-offs. Open-source software can be highly customizable but may require technical expertise to manage and secure. Closed-source software offers ease of use and integrated support but limits flexibility and user control.
The rise of open source isn’t just about philosophy. It’s about practicality. Here’s why so many modern organizations are betting on it:
Cost Efficiency
The majority of open-source software is free to use. It lowers the cost of ownership and minimizes vendor lock-in. This means more control over the budget and may result in significant cost savings.
Flexibility and Customization
With access to software’s source code, teams can tailor software to meet specific business needs, whether it’s integrating with internal systems or building custom features.
Faster Innovation
Open-source communities move quickly. New projects and accelerated development cycles bring products to market faster.
Improved Security and Transparency
Open codebases give more insight into potential security vulnerabilities. With active communities and regular updates, security issues are often identified and resolved faster than in closed systems.
Talent Attraction and Retention
Developers value working with open-source tools and contributing to meaningful projects. Supporting open source can help attract top engineering talent and foster a culture of innovation.
Ecosystem and Interoperability
Open-source technologies often follow open standards, making it easier to integrate with other tools and platforms. This supports more agile, scalable, and future-proof architectures.
Where Open Source Is Heading in 2026
Open source has matured. It’s the default foundation for many enterprise teams and not a cost-cutting exercise. Here are a few trends shaping the next chapter of open source evolution that should be on your radar:
The Market Will Grow
As the backbone of many businesses’ operations, open-source software has seen enormous growth in previous years, and it’s on course to expand at an even faster rate in the future.
A report by MarketsandMarkets projects that the open-source services market, at $21.7 billion in 2021, will reach $50 billion by 2026.
Commercial versions of open-source software exist because creators and companies monetize these long-term projects by offering additional features or services.
Commercialization and the Open Core Model
Companies are monetizing open source by offering enhanced versions, support, or additional features on top of free foundations. As organizations rely more heavily on OSS, they’re investing in better management: license audits, compliance frameworks, and automated tooling.
There Will Be a High Demand for Skills in Open Source Software Development
According to the Linux Professional Institute report 2024 Open Source Professionals Job Survey Report, half of the managers plan to increase hiring of open-source professionals.
But this presents a bit of a challenge to engineering leaders as well. They may have difficulty finding professionals in the space with the requisite skills and expertise.
This, perhaps, is why the vast majority are prioritizing the hiring of certified open-source professionals.
89% of respondents considered an employer’s open source policy when making job choices. Knowing how to work with open source tools is now a competitive skill. Whether it’s Kubernetes, Python libraries, or Git-based workflows, demand for OSS fluency is rising.
Users Will Consider More Open-Source Alternatives to Proprietary Software
With open-source software on the rise, it’s no surprise that an increasing number of users are turning to alternatives to closed-source software.
Security Will Be Underscored and Heightened
Security is one reason why so many commercial companies turn to open-source software. And now, developers are paying increasing attention to and heightening security measures. They will focus more on spotting security vulnerabilities and identifying tools to support any se
Embrace Open-Source Software Trends
For enterprises, open source isn’t a cost-cutting trend, but a control strategy. Done right, it reduces vendor lock-in risks, accelerates delivery, and supports audit-ready, scalable systems.
At BairesDev, we don’t just help clients adopt open source solutions; we help make them work at scale. From improving security posture to reducing vendor dependence, we’ve implemented solutions that are built to last. And where we can, we contribute back. Because open collaboration isn’t just good practice — it’s how progress happens.
We expect to see continued investment in tooling for security risks, license management, and operational visibility. The future of open source will be shaped less by novelty and more by how well it fits into complex, regulated environments.






