A multicloud computing approach means using multiple cloud computing platforms or providers to run different business operations. For example, a company might use one platform to host productivity tools, and another to create an environment for product development.
The motivation is clear: flexibility, resilience, and cost optimization. By paying only for what they use and distributing infrastructure across cloud platforms, businesses avoid the trap of over-provisioning on on-premise systems or relying too heavily on a single provider.
But this flexibility introduces risk.
Securing a Multi-Cloud Environment
With multiple cloud service providers, each with its own settings, tools, and standards, ensuring consistent security becomes a much more complex task.
You’re defending many—across geographies, platforms, and vendors. And while this setup can offer redundancy and uptime benefits, it also opens the door to:
- Inconsistent access controls
- Fragmented logging and visibility
- Policy misalignment
- Human misconfigurations
And when data moves between providers, it becomes harder to track, encrypt, and protect.
In this guide, we’ll walk you through how to build a multi-cloud security strategy that minimizes risk, maintains compliance, and ensures your cloud deployments stay secure—no matter how complex.
Understanding the Landscape
Multi-cloud environments are complex and diverse, comprising multiple cloud providers, services, deployment models, stacks, and configurations.
Each cloud comes with its unique security challenges and requirements.
- Public clouds – such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP) offer scalability and flexibility but also introduce security risks associated with shared infrastructure.
- Private clouds – provide more control and security, but can be more expensive and less scalable.
- Hybrid clouds – combine public and private clouds, offering a balanced approach to security and scalability.
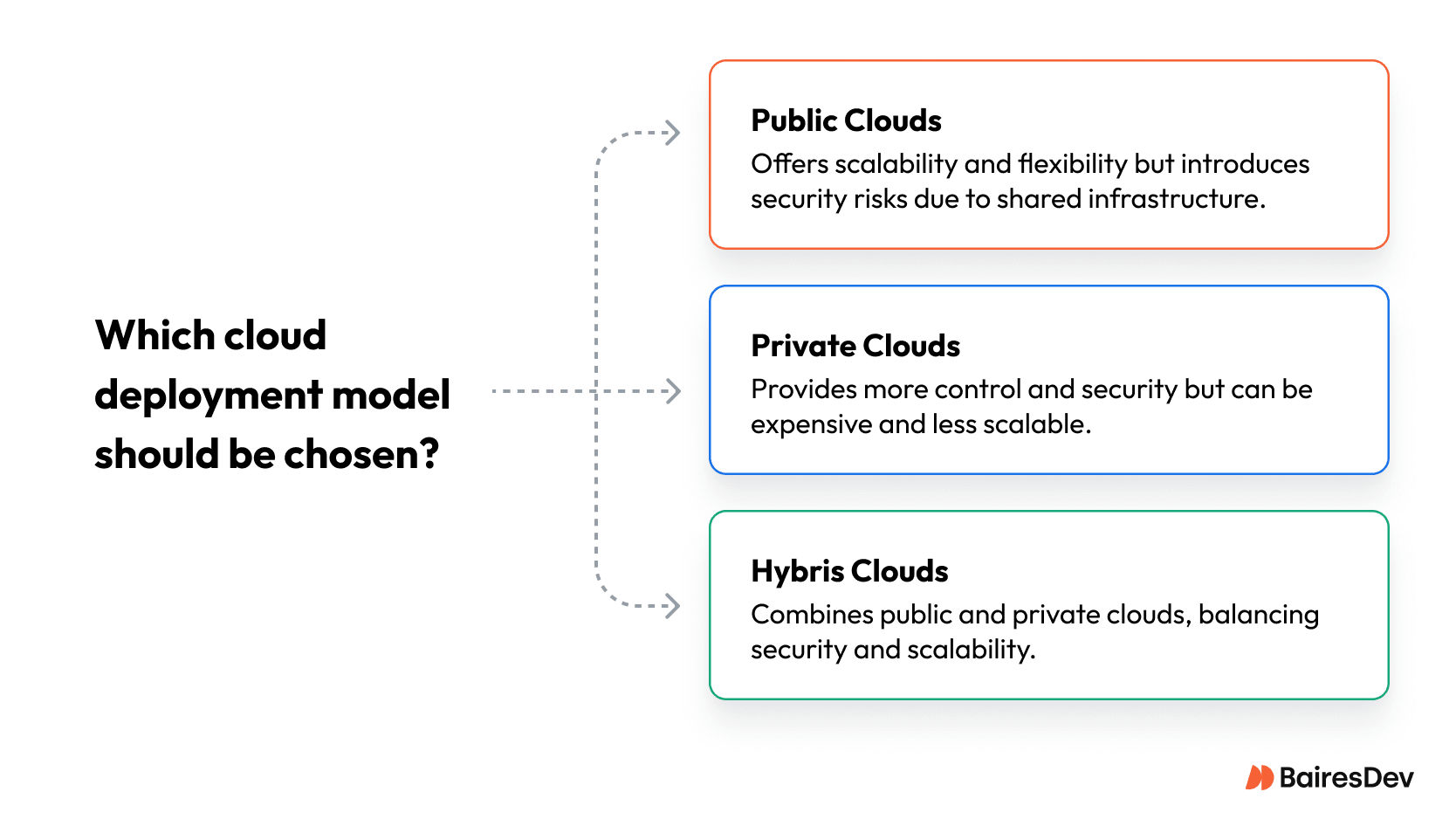
In a multi-cloud setup, all these systems need to cooperate, and your team has to ensure security across different vendors and stacks.
Key Multi-Cloud Security Challenges
Managing multiple cloud environments means juggling:
- Different APIs
- Unique access rules
- Varying compliance certifications
- Separate monitoring systems
This patchwork setup leads to security gaps, especially when companies attempt to extend policies designed for one cloud across all others.
Other pain points include:
- Shadow IT
- Non-standard encryption protocols
- Inconsistent identity verification
- Limited visibility into configuration drift
A robust multi-cloud security strategy ensures these differences don’t turn into vulnerabilities.
Cloud Security Posture Management: The Backbone of Control
A good securit posture gives teams continuous visibility and real-time flagging of issues—misconfigured permissions, weak encryption, or policy gaps. Automated remediation and compliance checking drive down risk while avoiding manual overhead.
According to Gartner, CSPM tools can cut misconfiguration-driven incidents by up to 80 %.
CSPM tools help organizations monitor and enforce security configurations across all their cloud deployments. They can:
- Identify misconfigurations
- Detect compliance violations
- Offer real-time alerts
- Automate remediation workflows
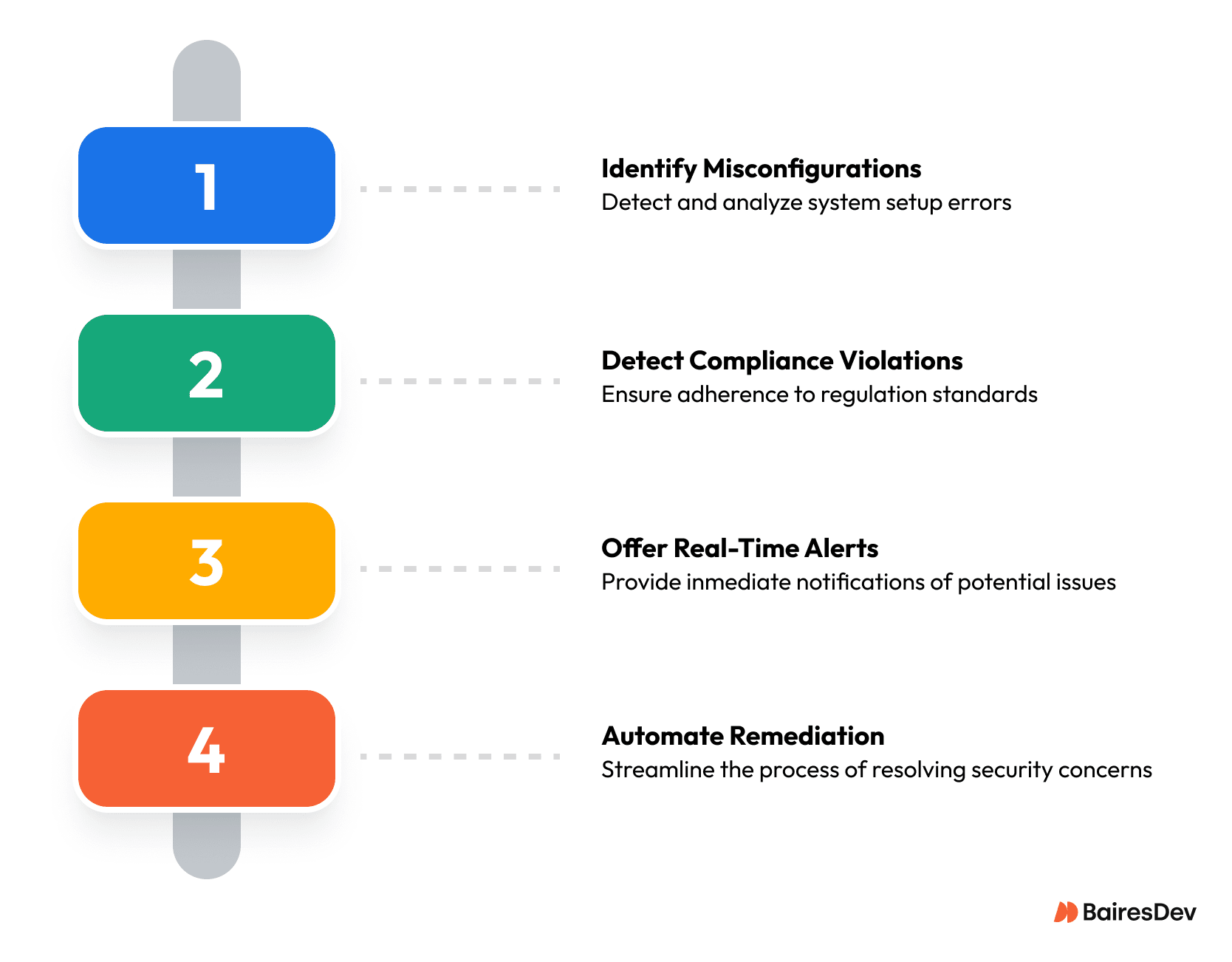
The value of CSPM is in its ability to provide a single view of risk across multiple clouds.
Whether you’re managing GCP projects or containerized workloads in AWS, a centralized CSPM solution reduces blind spots and builds a foundation for continuous security enforcement.
A recent Forbes Technology Council post advises, “Define and enforce a unified security policy configuration that connects all of the cloud providers your company uses.”
Automate Security Wherever Possible
Automation becomes especially critical when dealing with multiple cloud platforms that scale dynamically.
Cloud computing enables process automation, and that can include security operations as well. For example, new virtualized machines and containers should be subject to security scans. The Forbes Technology Council post states, “Automation is crucial to a successful multi-cloud security plan. By removing human error from deployment and management, you can significantly reduce your company’s risk.”
Organizations should create automated security management processes, such as configuration, patching, and audits. Utilizing automation tools can enhance security management within multi-cloud environments by streamlining tasks such as vulnerability scanning and threat remediation. The following video discusses cloud security tools.
Centralize Access Management
Access mismanagement remains the root cause of security breaches. Identity and Access Management (IAM) solutions provide a centralized framework for managing access to cloud resources.
IAM solutions include features such as multi-factor authentication, role-based access control, and least privilege access, reducing the risk of unauthorized access and data breaches.
By implementing IAM solutions, organizations can ensure that access to multiple cloud services remains secure, auditable, and compliant with regulatory requirements. A comprehensive approach to access management is a prerequisite for every professional cloud deployment.
Follow Cloud Security Best Practices
Once you have reexamined your security posture, considering a multicloud deployment, and automated as many processes as possible, use the following cloud security best practices to ensure the highest level of security.
- Consider compliance. In addition to providing a platform for running some company operations, cloud environments can help companies comply with the standards and regulations relevant to each industry.
- Exercise smart policy management. Infrastructure as a Service (IaaS) provider phoenixNAP suggests, “Companies should develop a set of security policies to enforce on all cloud environments and simplify security operations.”
- Employ data encryption and protection measures. A strong multicloud security strategy must include the encryption of data both at rest and in transit. Incorporating data protection measures within regular security audits and assessments is crucial to identifying vulnerabilities and ensuring compliance.
- Perform regular backups. Backups are just as important in multicloud environments as they are anywhere else. Use a separate backup for each cloud provider.
- Apply the principle of least privilege. Even your own employees can carry out a data breach. That’s why it’s important that each employee only has access to the environments necessary to perform their roles.
- Use tenant isolation. Using this method, operators ensure that each app and each environment run in separate tenants.
- Deploy multi-cloud monitoring. Each cloud environment will generate its own events, logs, notifications, and alerts. Set up a way to consolidate them in one location.
Built-in Security into Deployment, Not After
The best way to ensure security is to build it in when creating a multicloud environment. Cloud security provider Aqua Security Software recommends considering the following areas when setting up new platforms.
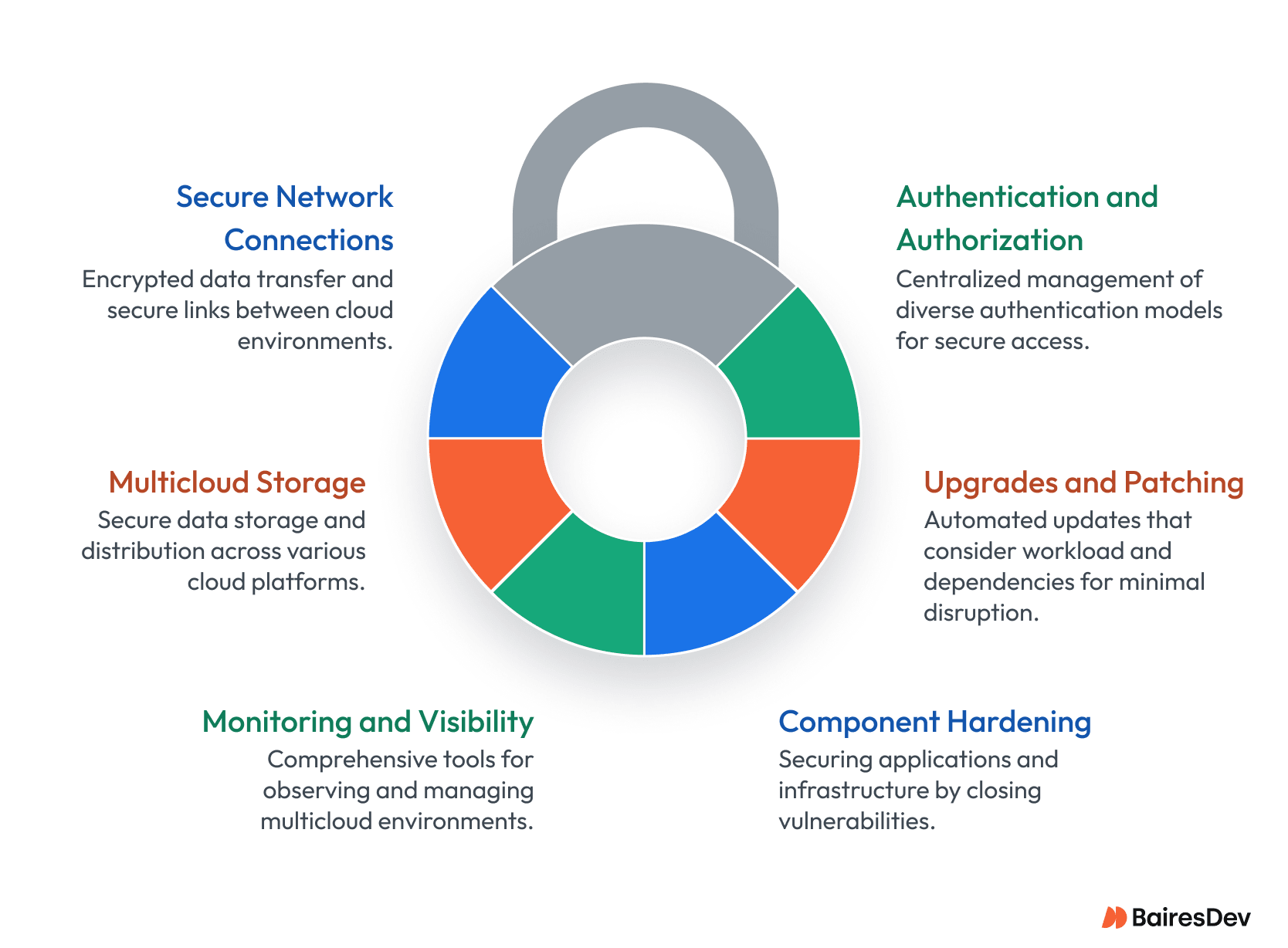
- Authentication and authorization
Find a framework that can support the different authentication models used by various cloud providers, but lets you define accounts, roles, and policies in a centralized manner.
- Upgrades and patching
Automate software upgrades and patches, ensuring that upgrades are sensitive to the workload, the infrastructure it is currently running on, and its dependencies.
- Component hardening
Hardening applications and infrastructure components involves closing unsecured ports, removing unnecessary software, securing APIs and web interfaces, and following the principle of least privilege.
- Monitoring and visibility
In a multicloud environment, you must have a tool that supports multiple clouds and enables visibility of the entire environment.
- Multicloud storage
Ensure that sensitive data is assigned to the most secure storage resources, distribute data geographically according to compliance obligations, and implement data loss prevention solutions that can identify data loss or exfiltration across multiple clouds.
- Secure network connections
Ensure safe data transfers between different cloud environments by implementing encryption and utilizing VPNs or dedicated links to safeguard data during transit, minimizing exposure to potential threats.
BairesDev’s Role in Multicloud Security
BairesDev works with large organizations that depend on multi-cloud deployments to deliver at scale, often under strict compliance obligations.
Our engineers embed security from day one, aligning with your internal policies and toolchains — not creating parallel processes you have to manage.
We ensure:
- Policy alignment from the start — integrating with your IAM, SOC, and compliance workflows.
- Secure development at scale — every commit is auditable, every deployment follows least-privilege principles.
- Consistent enforcement — our long-term, full-time teams apply the same controls across projects, clouds, and geographies.
- Continuity you can depend on — no handoffs to short-term contractors, no policy drift between engagements.
With 15+ years of enterprise delivery experience, 4,000+ full-time senior engineers, and proven success in heavily regulated industries, we help clients keep multi-cloud environments fast, flexible, and secure.
Frequently Asked Questions
What is the role of CSPM in enterprise cloud security?
CSPM (Cloud Security Posture Management) helps enterprises monitor and enforce security policies across multiple cloud environments. It identifies misconfigurations, ensures compliance, and enables automated remediation. For large organizations, CSPM is critical to maintaining consistent controls and avoiding gaps that can lead to breaches or audit failures.
How do we create a multi-cloud security architecture compliant across different regulatory frameworks?
Map each workload to its regulatory requirements (HIPAA, PCI-DSS, SOC 2, FedRAMP, GDPR, etc.) and enforce policies through a unified CSPM platform. We help clients configure cross-cloud compliance templates and automated audits that satisfy multiple jurisdictions without duplicating work.
What’s the most effective way to manage incident response in a multi-cloud environment?
Have a single incident response plan that covers all providers, with clear escalation paths and tooling that aggregates logs and alerts into one view. We work with clients to implement central SIEM integrations so incidents are detected and acted on quickly — regardless of where they originate.
How can we measure improvement in multi-cloud security posture?
Track KPIs like time-to-detect, time-to-remediate, number of critical misconfigurations, compliance audit pass rates, and security automation coverage. Enterprises we’ve supported typically see a 60–80% reduction in misconfiguration-driven incidents within the first year.






