A mature engineering organization runs on repeatable processes. Yet that repeatability collapses the moment a production-critical server is rebuilt by hand or a last-minute firewall rule is added without review.
Infrastructure as Code (IaC) places every environment definition under version control and treats it exactly like application source. The result is infrastructure provisioning that is transparent, testable, and auditable. For a CTO, the allure is straightforward: faster delivery that does not erode compliance or stability.
A mature engineering organization runs on repeatable processes. Yet that repeatability collapses the moment a production-critical server is rebuilt by hand or a last-minute firewall rule is added without review.
Infrastructure as Code (IaC) places every environment definition under version control and treats it exactly like application source. The result is infrastructure provisioning that is transparent, testable, and auditable. For a CTO, the allure is straightforward: faster delivery that does not erode compliance or stability.
From Manual Infrastructure to Codified Environments
Small teams can survive with a single systems engineer applying ad-hoc patches. Enterprises cannot. The gulf between those two realities frames the journey from manual builds to codified environments.
The Bottlenecks of Traditional Provisioning
Before IaC, every new environment unfolded through tickets and tribal knowledge. The release windows stretched because each modification required a unique runbook. Human error thrived, so staging never quite matched production, and post-release firefights became common. Too common for professional organizations.
Even when infrastructure configuration management tools eased some pain, the lack of an authoritative source of truth meant drift crept back in. Over time, inconsistencies could compound and turn into operational risk that auditors, security teams, and developers all felt in different ways.
IaC as a Foundation for Platform Engineering
Codifying environments changed that. Templates stored in Git establish an immutable record of intent, while pipeline hooks validate syntax, enforce policy, and block unsafe merges before anything reaches the cloud console. Teams begin to think in terms of reusable modules rather than one-off scripts, which accelerates onboarding and shrinks time to recover when systems fail.
In practice, IaC becomes the substrate for a broader platform-engineering push that layers service catalogs and self-service automation on top. The infrastructure team shifts focus from button-click provisioning to product management of the internal platform.
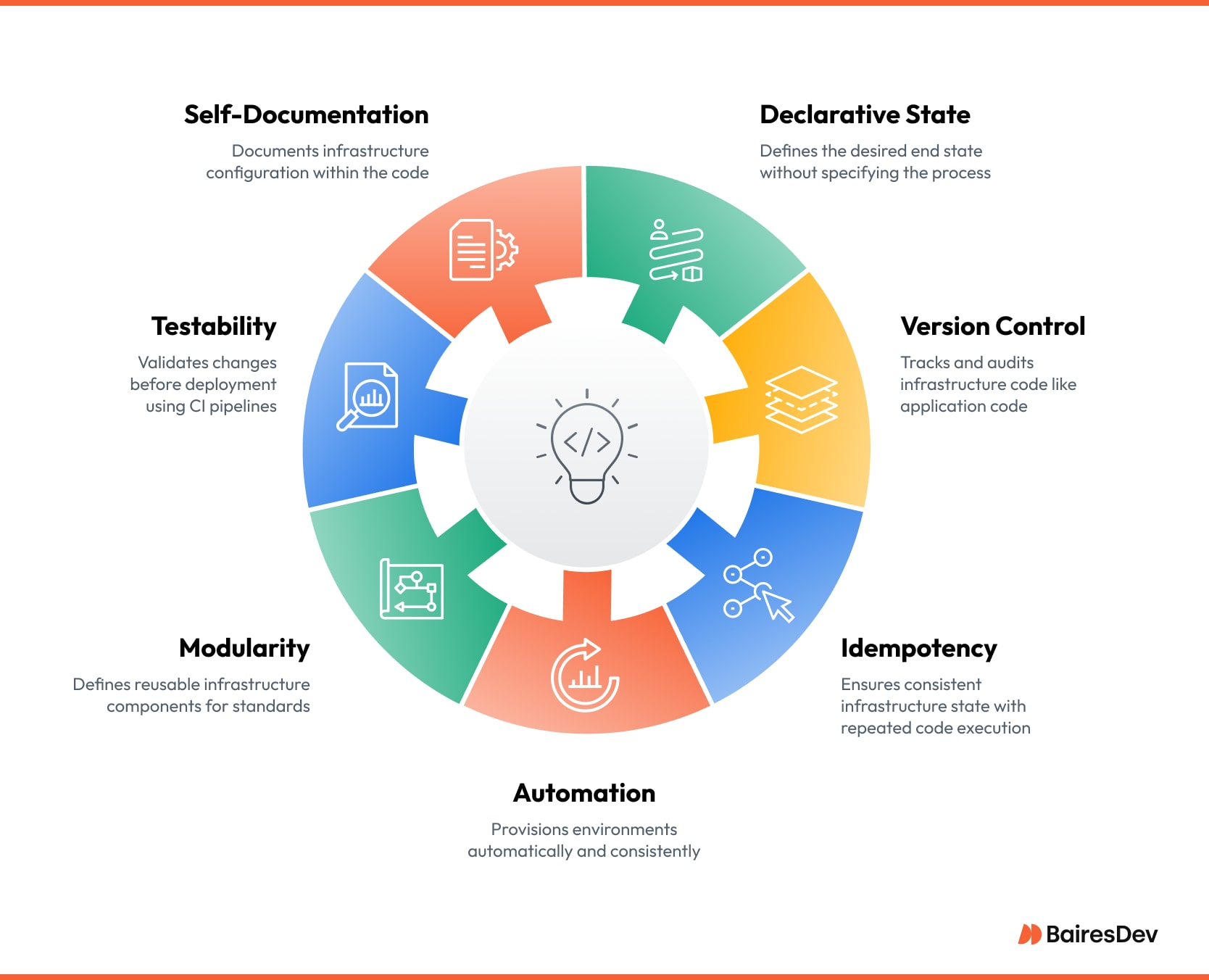
Core Principles of IaC for Modern Delivery Pipelines
Codifying servers is just the first step. Sustained value emerges when IaC complements continuous integration, observability, and governance workflows. The following principles anchor that integration.
Declarative vs Imperative Models
Declarative tools such as Terraform describe the desired state, e.g., an S3 bucket should exist, a load balancer should expose ports 80 and 443, and so on. The engine figures out the steps.
Imperative approaches like Ansible enumerate commands in sequence. Declarative syntax scales better for multi-cloud abstractions and policy enforcement, while imperative code shines when fine-grained orchestration is required. Most enterprises blend both, choosing the model that minimizes cognitive load for each task.
Source of Truth and Configuration Drift
Committing environment definitions to a version control system gives every change a diff, a review, and a rollback path. State files and locks guard against parallel edits. Yet drift remains a threat whenever someone bypasses the pipeline.
Successful teams schedule reconciliation jobs that compare existing infrastructure to the repository and open pull requests when divergence appears. Over time this closed-loop feedback converts reactive firefighting into proactive hygiene.
Secrets, Dependencies, and Ephemeral Environments
Automated pipelines cannot embed plaintext credentials. Infrastructure automation solutions range from cloud-native managers to tools such as Vault, integrated through short-lived tokens injected at runtime.
Dependency graphs add complexity: an application stack often requires a database, message queue, and network policies built in precise order. Declarative orchestrators resolve those relationships automatically, which allows entire environments to spin up for every pull request, run tests in isolation, then vanish. The payoff is faster feedback for developers and reduced impact on operations.
Enterprise IaC Tooling Ecosystem
The market offers enough IaC tools to overwhelm even veteran architects. Rather than list every logo, focus on the categories that shape day-to-day practice and on the questions a director of platform engineering needs answered before adding a new dependency.
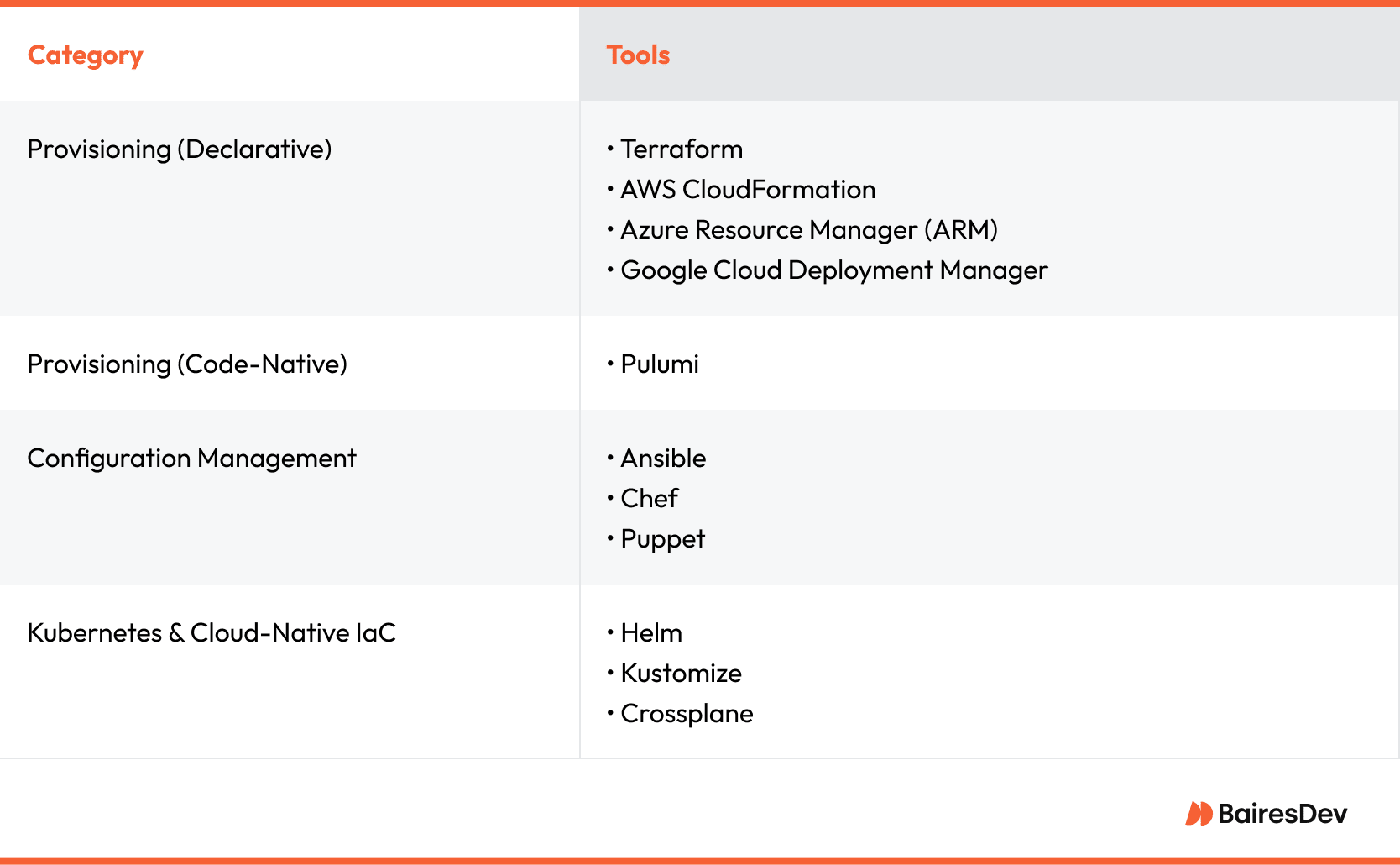
Infrastructure Provisioning Tools
At the center sit the declarative engines. Terraform remains the default when you must span more than one cloud. It translates high level intent—VPC, subnet, encrypted volume—into cloud provider APIs yet still lets you codify guardrails in reusable modules.
Cloud-native templates such as AWS CloudFormation or Azure Resource Manager deliver tighter integration with their respective ecosystems and often enable earlier access to new services. Choose the native option when your organization relies on a single cloud and values first-party support. Choose Terraform, Pulumi, or Crossplane when portability, consistent linting, and a common language outweigh bleeding-edge features.
Configuration Management and Orchestration
Declarative IaC tools finish part of the job. Once a virtual machine exists, the operating system, runtime, and application services still require care. Ansible and Chef excel here. Ansible uses readable YAML and pushes changes over SSH, which keeps network rules simple.
Chef employs an agent model that reports compliance back to a central server, a win for teams bound by regulatory audit requirements. On Kubernetes clusters, you can treat Helm charts or Kustomize overlays as the infrastructure configuration tier, pushing new application images and sidecar versions while Terraform stands back. The key is assigning each layer a single owner so responsibilities never blur.
Integration with CI and CD, Observability, and Policy as Code
Infrastructure code belongs in the same pipeline as application code. Popular setups pin a Terraform plan stage early in the CI run, then block the merge until automated policy checks approve the change. Sentinel, Open Policy Agent, and Conftest specialize in those guardrails. Observability comes next.
Exporter modules publish metrics on apply duration, drift events, and plan-failure counts. Feeding these numbers into Prometheus or Datadog gives leadership a live pulse on the platform. The outcome is a delivery chain that surfaces risk early, measures reliability continuously, and enforces standards without slowing velocity.
Strategic Benefits for Engineering Organizations
Executives rarely green-light a tooling overhaul for novelty. IaC must prove it can raise throughput while lowering operational risk. The following outcomes demonstrate the payoff.
Scaling Without Chaos
A repeatable template lets a team clone an entire region in minutes. More importantly, it lets them retire that region just as quickly when traffic patterns shift. Capacity planning shifts from calendar meetings to code reviews, and infrastructure spend tracks demand rather than forecast error. Engineers gain confidence that the each new environment will look and behave exactly like the first, which frees them to innovate above the platform instead of wrestling with it.
Reducing MTTR and Incident Recovery Time
When every resource is declared in a repository, rollback becomes a git revert followed by a pipeline run. Mean time to recovery drops because no one scrambles to remember which undocumented tweak restored service last quarter. Postmortems improve as well. Teams can diff the faulty commit against the last healthy state and see precisely what changed. That clarity accelerates root-cause analysis and informs better guardrails for the next cycle.
Auditability, Compliance, and Governance
Regulators and security officers ask two questions: who changed the system and why. IaC answers both automatically. Pull-request history ties every modification to an approver. Policy engines assert that encryption, least-privilege roles, and network boundaries are in place before the change ships. Annual audits become a matter of exporting reports rather than tracing manual checklists. The organization gains demonstrable proof of control without adding paperwork that slows delivery.
IaC Adoption Considerations and Common Pitfalls
Rolling out Infrastructure as Code is seldom a straight line. The effort touches source control, cloud governance, and team culture in equal measure. Before the first template lands in Git, leaders should map the terrain and plan for the snags that even seasoned DevOps engineers hit.
The Hidden Complexity of IaC at Scale
A single repository looks tidy until the fourth team forks it and the state file balloons. Merge conflicts arise when two teams add infrastructure resources to the same module on Friday afternoon. Locked states delay production fixes because someone forgot to release their CLI session.
These issues are normal growing pains, not signs of failure. Treat them the way you would treat application debt: refactor, modularize, and invest in automated tests that guard critical paths.
Organizational Maturity and Cross-Functional Alignment
IaC succeeds when every environment change flows through the same review gates that application code follows. That demands cooperation among security, ops, and development. If security teams still rely on spreadsheet approvals, build an automated policy check in the pipeline and prove it reduces toil.
When developers spin up test stacks outside the sanctioned development process, invite them to shape the shared modules rather than block them outright. Buy-in grows when platform engineers frame IaC as an enabler instead of a police force.
Training, Versioning, and Change Control
Most engineers learn a new language by reading production code, but IaC files can be dense. Budget time for internal workshops that walk through a real module from variables to outputs.
Pair new contributors with an experienced reviewer during their first merge so that best practices stick. Version your modules the same way you version libraries. Tag every release, write changelogs, and communicate deprecation windows well in advance. The result is predictable upgrades instead of weekend fire drills.
Looking Ahead: The Future of IaC
Infrastructure as Code has shifted from niche practice to baseline expectation, yet the field continues to evolve. Tomorrow’s pipelines will look different from today’s YAML-heavy jobs.
Toward Policy-Driven Self-Service Infrastructure
Platform teams are already wiring policy engines into pull requests. The next step is surfacing compliant templates inside internal developer portals. A staff engineer requests a Kafka cluster, selects a performance tier, and watches the portal generate a pull request that includes all required guardrails. Approval becomes a quick glance rather than an hour of checklist reviews. The move turns governance into a background service that never slows delivery.
IaC Meets AI and Predictive Automation
Machine learning is edging into infrastructure management. Early experiments analyze past changes, detect patterns that precede incidents, and propose safer resource configurations before code reaches production.
These tools will not replace human judgment or all manual processes, but they will help organizations manage infrastructure faster by identifying issues that busy teams might overlook. As the models improve, expect feedback loops that refine templates and policies in near real time, bringing another layer of resilience to the platform.
Final Thoughts: Codifying Infrastructure Signals Operational Maturity
A modern software organization is measured by how predictably it can move. Infrastructure as Code turns every subnet, policy, and operating system build into an artifact that teams can inspect, test, and improve. Leaders who embrace the practice see faster product cycles, smaller incident windows, and an audit trail that never depends on hallway knowledge.
The technical lift is real, yet the payoff of automated infrastructure is a platform that scales with the business rather than against it. For engineering teams under pressure to move fast without compromising reliability, codifying infrastructure is no longer optional. It’s time to implement IaC and make it a part of your delivery culture.
Frequently Asked Questions
How do IaC frameworks differ from traditional configuration-management tools?
Think of an IaC framework as the blueprint generator. It defines the cloud resources you want and stores them in version control. Configuration-management tools like Ansible or Chef step in afterward to lay down packages, users, and service settings inside those resources. You get two layers that complement each other rather than compete.
Can our team use a single IaC workflow across multiple cloud providers?
Yes, although you will need careful module design and clear state-management boundaries. Most enterprises pick Terraform because its providers abstract vendor APIs. Just remember that the lowest common denominator rule applies: if only one cloud supports an interactive configuration tool or a specific load-balancing feature, you either code a conditional or accept vendor lock-in for that piece.
What guards against human error in IaC workflows?
Everything lands in version control first. Peer reviews, policy scanners, and automated plan outputs highlight risky changes before they touch live infrastructure. If someone merges a mistake, a simple rollback of the configuration files followed by the pipeline run restores the desired infrastructure state without late-night console clicks.
How does load-balancer configuration translate into code?
You declare listeners, target groups, and health checks, and the IaC engine issues the correct API calls behind the scenes. Need to add a blue-green deployment route? Update a few lines in the configuration file, commit, and let the automation tool roll out the new infrastructure without manual configuration steps.
Do we have to learn a domain-specific language to get started?
Not necessarily. Terraform relies on HCL, which feels close to JSON but friendlier. Pulumi lets you write infrastructure in TypeScript, Python, or Go if that aligns better with your team’s existing skill set.
How early in the development cycle can we spin up production-like environments?
With a solid IaC pipeline, you can create an isolated, production-like stack every time a developer opens a pull request. Dependency-management logic in the templates handles databases, message queues, and secrets, so tests run on something that mirrors production instead of a mocked sandbox.






