A hospital’s unencrypted database gets breached, exposing 500,000 patient records. The cost? A staggering $10.1 million.
That’s just the beginning. Add regulatory fines, legal battles, and destroyed patient trust, and you’re looking at an engineering leader’s worst nightmare. Think it can’t happen to your organization? Think again.
In just the first half of 2025, over 31 million individuals had their protected health information (PHI) exposed in 379 large healthcare data breaches reported to the HHS Office for Civil Rights. That accounts for a substantial portion of the nearly 281 million records exposed in all of 2024.
While HIPAA-compliant encryption requirements may seem like a regulatory maze, they’re actually a blueprint for building robust and secure healthcare systems. The question “Does HIPAA require encryption?” comes up often, and the answer isn’t a simple yes or no. The reality is that HIPAA data encryption requirements have become fundamental to modern healthcare security.
Understanding HIPAA’s Encryption Framework
Does HIPAA require encryption? Let’s start with a truth that might surprise you: HIPAA doesn’t actually mandate encryption everywhere.
Shocked? Here’s the catch. While encryption is technically “addressable” rather than “required,” choosing not to encrypt patient data is like choosing not to lock your front door because you have security cameras. Sure, you can do it, but good luck explaining that decision when something goes wrong.
Required vs. Addressable Controls
Here’s where things get interesting. When HIPAA labels encryption as “addressable,” they’re really playing a clever game of regulatory chess. According to HHS guidance, you have three moves:
- Implement the addressable encryption specifications
- Implement an alternative measure that accomplishes the same goal
- Document why no action requirements exist in their environment
The U.S. Department of Health and Human Services (HHS), in coordination with the National Institute of Standards and Technology (NIST), outlines encryption expectations in the HIPAA Security Rule.
Under the rule, organizations must conduct a risk analysis to determine whether encryption is reasonable and appropriate for their environment. If it’s not implemented, that decision must be justified, documented, and compensated by appropriate security measures that achieve the same objective.
In the current security landscape, it’s increasingly difficult to make a credible case for skipping encryption. The volume and severity of healthcare data breaches, combined with evolving enforcement trends, have made encryption a de facto expectation. For most organizations, the question isn’t whether to encrypt, but how to do it thoroughly and correctly.
“Encryption is ‘addressable,’ not ‘optional.’ HIPAA-covered entities must assess the reasonableness of implementing encryption and document their rationale if they choose otherwise.” – U.S. Department of Health and Human Services (HHS) Security Rule Guidance
Key Regulatory Requirements
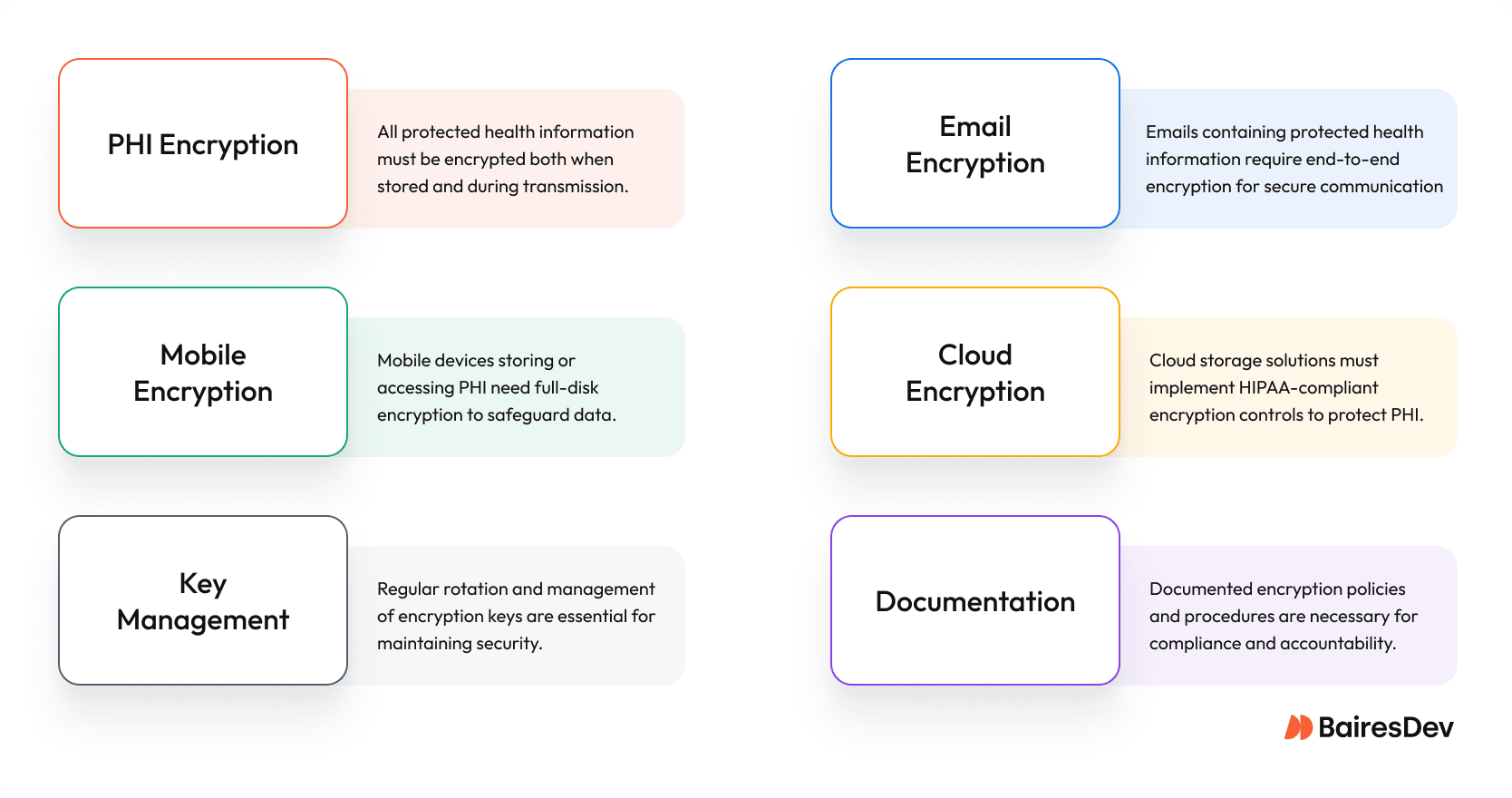
HIPAA data encryption requirements encompass two primary areas. When implementing HIPAA encryption protocols, you’re fighting to protect:
- Data at Rest: Any data stored within a HIPAA-regulated system, sitting in your databases, file systems, or that forgotten backup drive in the closet, must be protected under the same encryption standards.
- Data in Transit: All those electronic health records zipping across your networks, whether they’re heading to the cloud or just down the hall
NIST SP 800-66 Rev.2 breaks HIPAA’s requirements into actionable technical steps, while the broader NIST Cybersecurity Framework 2.0 offers a strategic model for aligning encryption and risk management with business priorities.
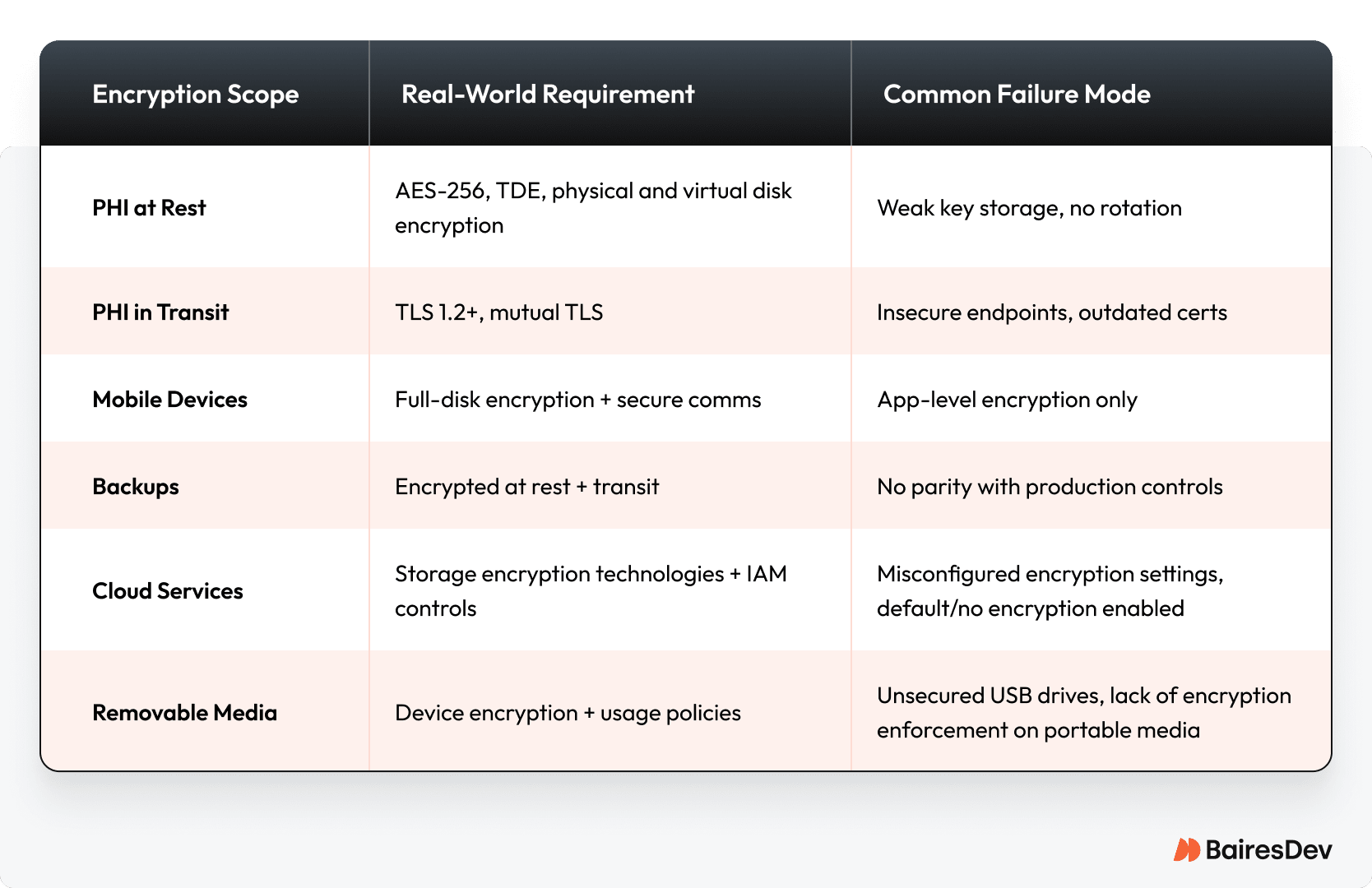
Here’s a quick reference for where encryption applies and where breakdowns most often occur.
Common Misconceptions
Let’s bust some myths that could get you in trouble:
- “Any encryption method will do.”
Wrong. HIPAA compliance requires the use of strong encryption techniques and standards such as Advanced Encryption Standard AES-256 and TLS 1.2 or higher. Outdated or weak encryption technologies don’t hold up under audit or attack. - “Our cloud provider has great encryption solutions.”
Cloud platforms offer various encryption technologies, but configuration and enforcement are your responsibility. HIPAA places the compliance burden on the covered entity. It’s on you, not your vendor. - “HIPAA encryption is optional.”
While technically “addressable,” encryption is expected unless you can justify and document a viable alternative. Foregoing encryption in 2025 is difficult to defend with regulators, healthcare providers, or patients.
HIPAA Encryption Standards and Implementation
Ever wonder what keeps healthcare CISOs up at night? It’s way more than just encrypting data. It’s about getting it absolutely right, making sure patient info and other sensitive data is super protected and compliant, especially with all the new threats popping up.
Let’s talk FIPS 140-3. This is the real deal, the standard that shows you’re serious about security, not just checking a box. It’s not just another rule; it’s a key benchmark for cryptographic modules, making sure the tech keeping sensitive patient data safe meets tough federal standards.
For healthcare systems, hitting and keeping FIPS 140-3 validation isn’t optional—it’s essential to building trust, lowering risks, and showing you’re totally committed to data privacy. It means your encryption has been tested and validated by certified labs, giving you a level of confidence no other standard can touch.
FIPS 140-3 validation is how healthcare organizations go from just saying they protect patient data to actually proving it, whether it’s during an audit or a cyberattack. Without FIPS 140-3? You’re walking a minefield of potential weak spots, big fines, and a reputation risks.
Data at Rest
Data at rest isn’t data at peace. It’s a sitting duck. Every database backup, file export, and archived record is a target. Here’s how to secure every entry point:
Database Encryption:
- Field-level encryption for your most sensitive information
- Transparent Data Encryption (TDE) for an additional layer of security
- Encryption keys are stored separately from the data they protect
File/Object Storage:
- Encrypted file systems that prevent unauthorized access
- Object storage that is highly secure
- Backup systems that ensure electronic PHI integrity and availability
Don’t assume cloud provider defaults meet your requirements! Review config and encryption status across all storage tiers, and be ready to implement additional security measures.
Working in the cloud? AWS’s HIPAA-eligible services give you industrial-strength tools, but remember that you still need to know how to use them.
Data in Transit
Every piece of data zipping across your network is a potential breach. If it’s not encrypted in transit, you’re exposed. It’s that simple. That data, especially when it includes PHI, must be encrypted in transit using reliable, standards-based protocols.
NIST SP 800-52 Rev. 2 defines expectations for secure communications. Meeting these transmission security guidelines is not optional. Secure data transfer is foundational to HIPAA-aligned system design.
TLS Requirements
- TLS 1.2 or higher must be enforced system-wide. Earlier versions are considered insecure and non-compliant
- Certificate-based authentication that proves you are who you say you are
- Regular certificate rotation because yesterday’s secure is tomorrow’s vulnerable
API Security
Want to keep your APIs from becoming the next headline? Here’s your checklist:
- Ensure all endpoints are encrypted and authenticated
- Mutual TLS that treats trust like nuclear launch codes
- API gateways that authenticate every request without fail
Mobile Considerations
Mobile devices in healthcare are useful but potentially dangerous. Lock them down with:
- Certificate pinning that stops man-in-the-middle attacks cold
- VPN tunnels or TLS-based secure transport to securely access PHI
- Messaging protocols with built-in encryption and session controls that keep patient chats private
Email and Communication Security
Healthcare communication systems require special attention. Here’s what HIPAA compliance means for your messaging systems:
Email Encryption Requirements:
- End-to-end encryption for all PHI-containing emails
- Secure email gateways that enforce encryption policies
- Automated scanning to prevent accidental PHI exposure
- Recipient verification before message delivery
Secure Messaging Considerations:
- Encrypted messaging platforms for internal communication
- Secure patient portals for protected health information sharing
- Audit trails for all PHI-related communications
- Data loss prevention (DLP) to catch unencrypted PHI
Architecture and Implementation Challenges
At BairesDev, we’ve seen healthcare organizations tackle these challenges head-on. Here’s what separates the winners from the headlines:
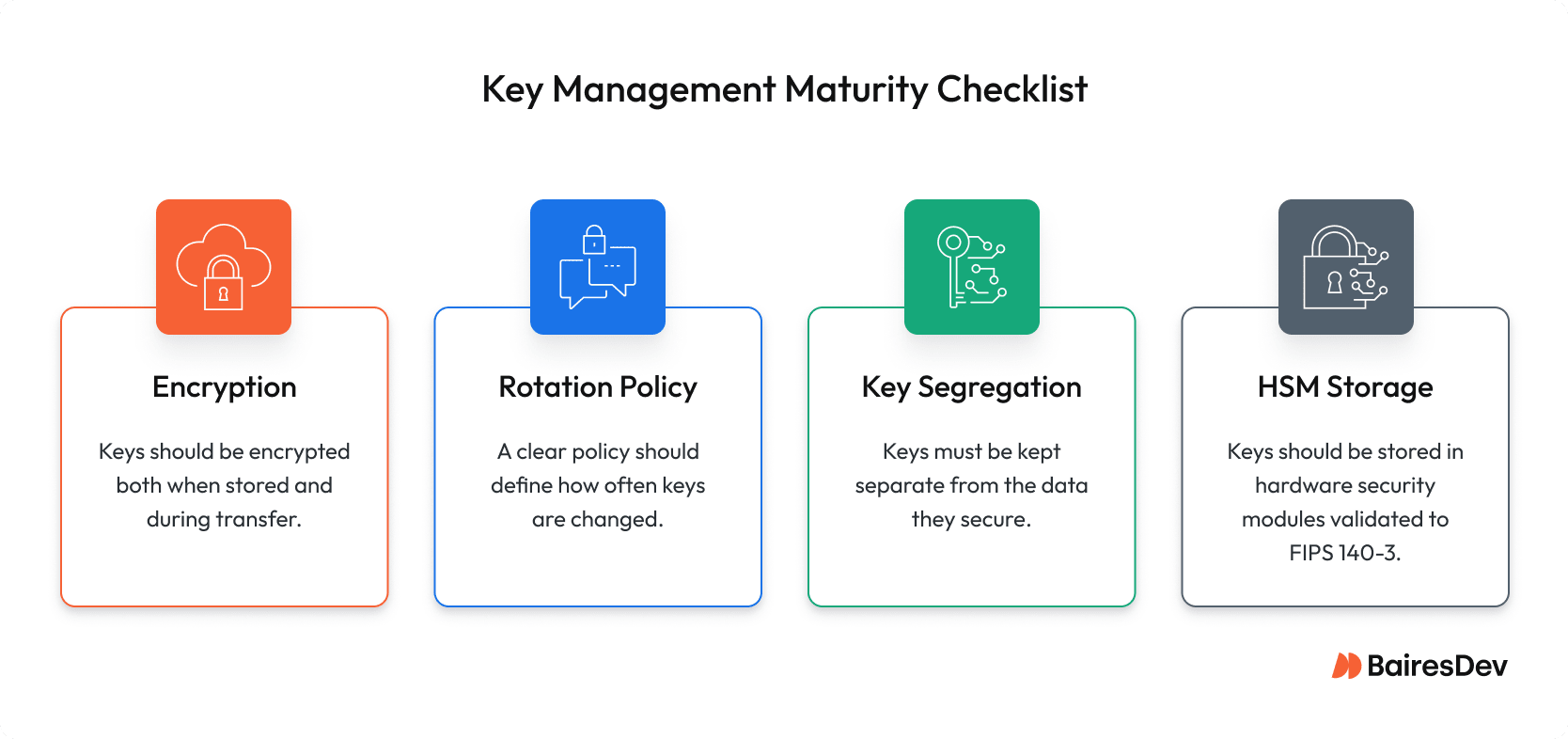
Key Management Rules
Think your encryption is solid? Your keys might tell a different story. Here’s what you need:
- Duty segregation that makes inside jobs nearly impossible
- Strict key rotation schedules
- Backup procedures that ensure you’re never one lost key from disaster
- Hardware Security Module (HSM) to protect and manage those keys
Integration with Legacy Systems
Do you have legacy systems? You’re not alone. Here’s how to bridge the old and new:
- Middleware that speaks both ancient and modern
- Compensating controls for systems too old to encrypt
- Migration strategies that don’t require a time machine
Third-Party Service Considerations
Are you sure all vendors have security covered? Think again. If you want to maintain HIPAA compliance, you need to be selective when it comes to vendors:
- Choose vendors with a strong track record in regulated industries. Look for those who’ve delivered complex, high-availability systems in healthcare, finance, or government.
- Work with teams that offer scale, maturity, and specialized roles—not boutique shops or freelance networks—so security responsibilities don’t fall through the cracks.
- All business associates must sign a Business Associate Agreement (BAA) outlining their responsibilities for encryption and transmission security under HIPAA.
- Validate that encryption practices are embedded into the vendor’s delivery lifecycle, including design reviews, DevSecOps processes, and IaC baselines.
- Prioritize partners that can provide independent attestations (e.g., SOC 2, ISO 27001) and operate in alignment with frameworks like NIST, HITRUST, or HIPAA.
- Ensure continuous collaboration, as effective vendors should integrate with your team’s workflows, tooling, and change control processes, not operate in silos.
Cloud Infrastructure Compliance
HIPAA encryption in the cloud isn’t just about checking boxes in your Google Cloud console. Your cloud HIPAA strategy needs:
- Configuration that would make a security auditor smile
- Cross-region strategies that keep data safe across borders
- Backup encryption that treats test data like production data
- Monitoring that catches issues before regulators do
Building a HIPAA-Compliant Security Program
Building a security program is like constructing a complex structure. The stakes are incredibly high, and you can’t simply rebuild if something collapses.
Access Control Integration
Your encryption algorithms are only as good as your access controls.
Strong access control starts with the basics: role-based access control (RBAC) and multi-factor authentication (MFA). RBAC limits what users can see and do based on their job function, so no one has more access than they need. MFA adds another layer of defense, especially for remote access or cloud-based systems where stolen credentials alone shouldn’t be enough.
But it’s not just about who has access—it’s about when and why. Just-in-time permissions help reduce long-standing elevated privileges, and regular access reviews catch accounts or roles that may have slipped through the cracks. Put simply: good access control is a living system, not a one-time setup.
Audit Logging Requirements
The Cloud Security Alliance puts it best: if you’re not logging it, it might as well not exist. You need:
- Key usage tracking that spots suspicious patterns
- Access monitoring that catches both mistakes and malice
- Configuration tracking that answers “who changed what and when?”
- Log reviews that someone actually reads
Breach Notification Protocols
Nobody plans to fail, but you’d better plan for failure. In breach scenarios, the ability to decrypt protected health information (PHI) is what often triggers the breach-notification timeline. Your checklist:
- Incident response that moves faster than Twitter
- Risk assessments that tell you how bad it really is
- Notification procedures that keep you legal
- Documentation that keeps lawyers happy
Team and Process Considerations
The best encryption on the planet is worthless if your process is broken. Your technology isn’t the weak link—your team and your strategy are.
ROI, TCO, and Business Alignment
Security investments, especially around encryption, shouldn’t be seen as sunk costs. They’re directly tied to business continuity, regulatory risk reduction, and long-term scalability. Strong encryption practices can reduce breach impact, lower the cost of audits, and even improve deal velocity with enterprise buyers who expect compliance baked into your architecture.
While upfront costs (like HSMs, policy automation, or training) may raise eyebrows, the long-term TCO is often lower than piecemeal fixes after something breaks. Leaders who plan for encryption as part of system design, and not just as a reaction to legal pressure, are better positioned to scale without constantly hitting roadblocks or surprises.
DevSecOps Alignment
Security isn’t just the security team’s problem anymore. Encryption controls require regular testing and monitoring procedures, especially in environments where drift or misconfiguration can lead to compliance gaps:
- Automated testing that catches issues before deployment
- Security scanning that never sleeps
- IaC validation that prevents configuration drift
- Training that makes security everyone’s job
Team
Encryption programs only succeed when the team behind them is equipped to make smart decisions. That means onboarding new engineers with clear security standards, offering practical upskilling on HIPAA requirements, and building a culture where secure defaults are expected, not optional. Teams need time, training, and context to get this right.
And don’t stop at your internal staff. Vendors, contractors, and nearshore teams also need to understand your expectations around data protection and compliance. Encryption is a shared practice that only works when everyone’s aligned.
Best Practices and Strategic Recommendations
The best way to stay ahead of HIPAA encryption challenges is to treat them as an ongoing program, not a one-time checklist.
Start by mapping where encryption is used across your systems. Look for inconsistencies, outdated methods, or areas where data might be moving unprotected.
Then build a roadmap. It doesn’t have to be perfect, but it should show progress over time and make sense to both your team and executive stakeholders. Roadmap implementation must also make monitoring part of your regular workflow, not something you scramble to do before an audit. Validate that your controls are working, and revisit them when your systems or vendors change.
And finally, get in the habit of reviewing decisions. Encryption standards evolve, tools shift, and what worked last year might not cut it now.
Avoidable Pitfalls
Learn from others’ mistakes:
- Thinking cloud compliance is automatic
- Treating complex public key management as an afterthought
- Monitoring only what’s easy to see
- Trusting vendors blindly
Final Strategic Takeaways
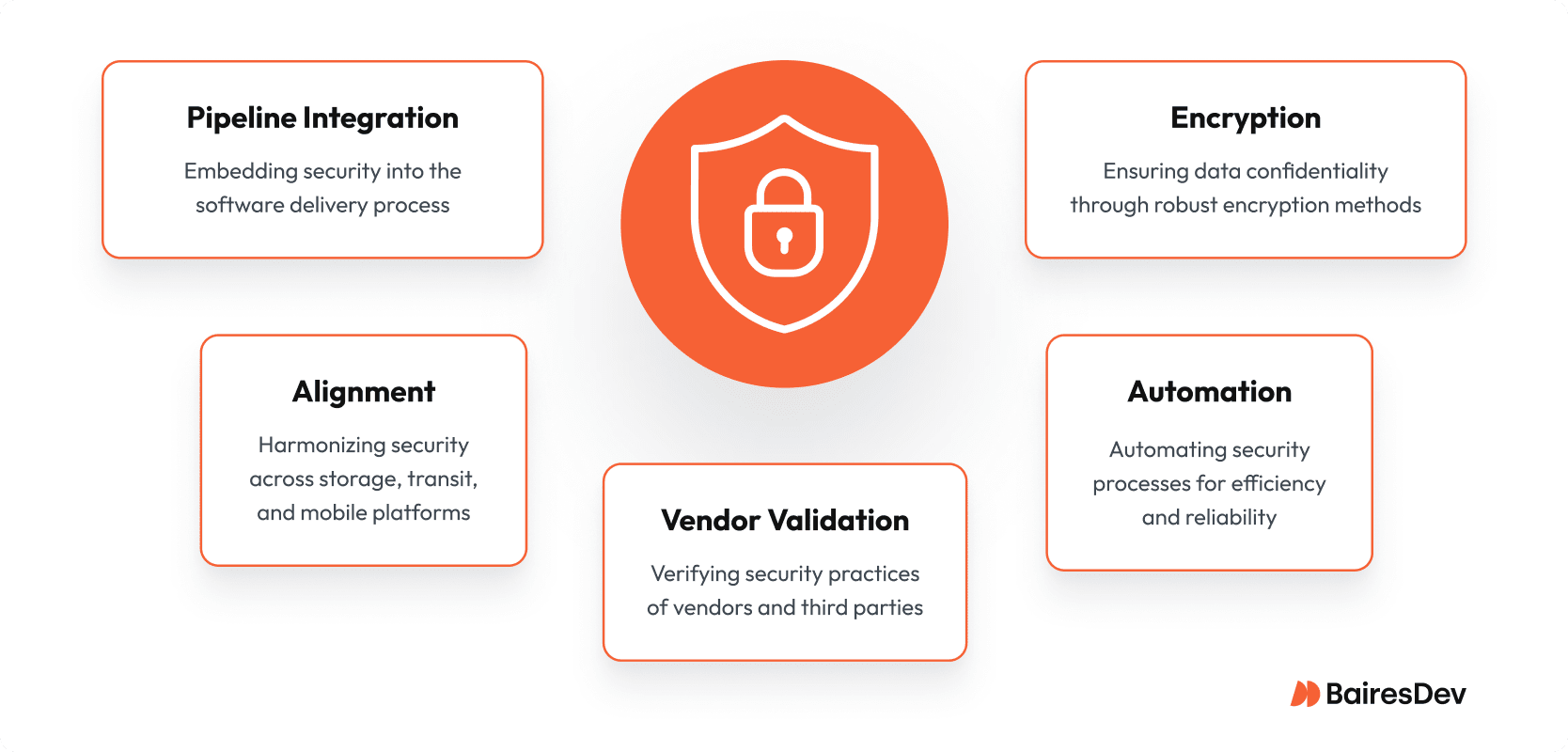
- Treat encryption as a foundational architecture decision
- Align storage, transit, and mobile strategies from the outset
- Validate vendor and third-party practices
- Automate monitoring and key rotation
- Integrate security into delivery pipelines
Conclusion: Security That Works
Here’s the bottom line: Meeting HIPAA encryption requirements isn’t just about avoiding fines. Proper HIPAA-compliant encryption is about protecting patients and your organization’s future. The tools are there. The standards are clear.
The choice is yours: encryption isn’t just a security control. It’s a foundational design decision that affects delivery velocity, audit readiness, and long-term risk exposure. Because in healthcare tech, security is a promise we make to every patient.
BairesDev’s Perspective
BairesDev has helped multiple healthcare organizations secure HIPAA-compliant applications across AWS, Azure, and GCP. Our distributed teams bring encryption, infrastructure-as-code, and automated compliance validation together, so engineering leaders can scale securely without compromising speed.
The No-Excuses HIPAA Data Encryption Checklist
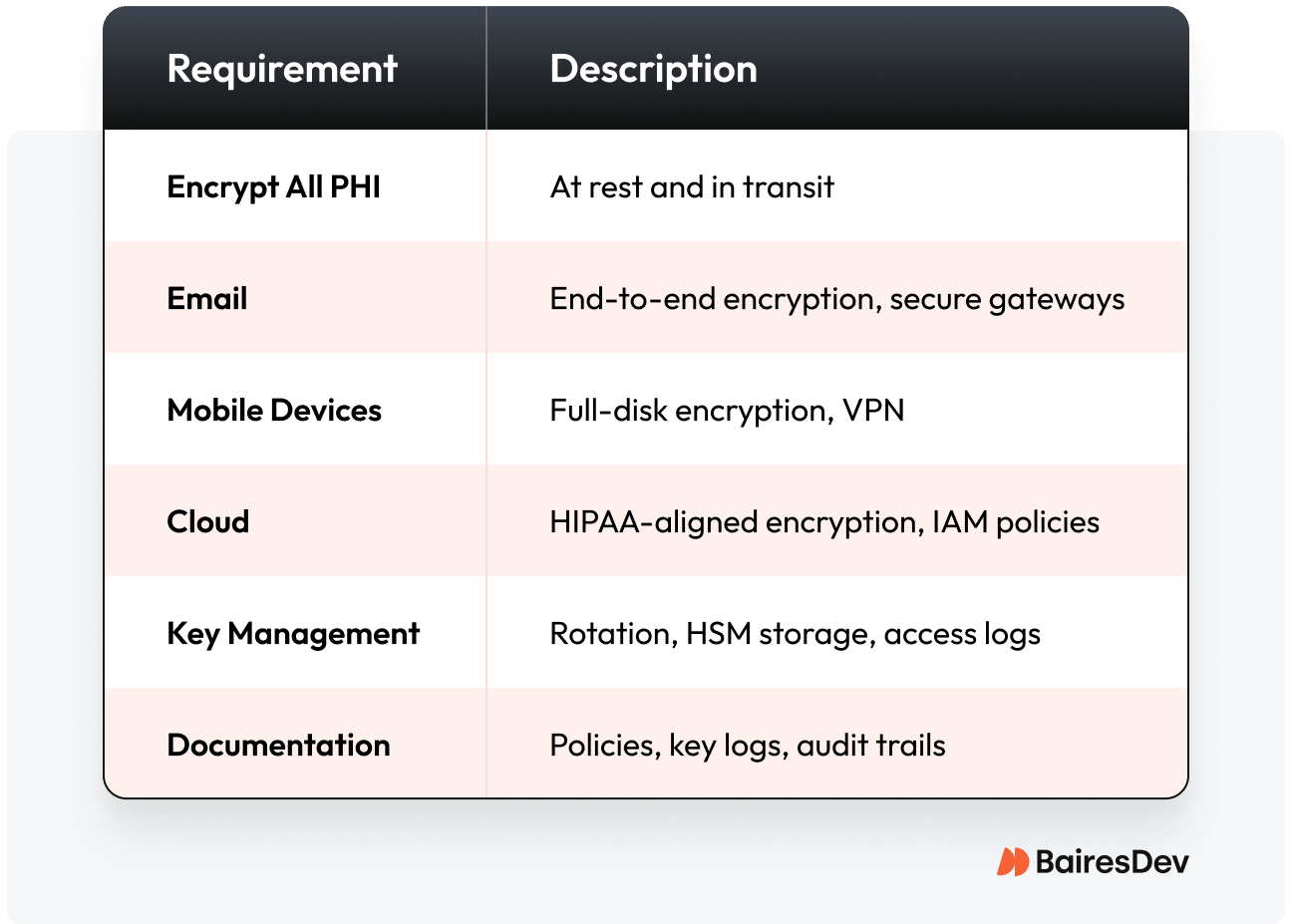
Frequently Asked Questions
Which vendor-due-diligence questions catch most encryption gaps?
Focus on key management and proof of practice. Ask for specifics on their key rotation intervals, how they segregate key access from data access, and if they store keys in FIPS 140-3 validated HSMs. Move from trust to verification by demanding their latest penetration test report that covers cryptographic controls and their specific incident response SLA for a compromised key.
If we use AWS/GCP/Azure KMS, are we automatically compliant?
No. Cloud key-management services are HIPAA-eligible, but compliance hinges on how you configure IAM, logging, key rotation, and shared-responsibility boundaries. Auditors expect documented policies plus evidence that controls are active in every account and region.
Will AES-256 or TLS 1.3 add noticeable latency to our EHR system?
For modern CPUs and NICs, encryption overhead is typically <2 ms per transaction. Performance hits usually stem from mis-sizing TLS handshakes or double-encrypting traffic. Benchmark in staging, enable TLS session resumption, and offload crypto to hardware where possible.
How do I prove “addressable” controls are met if we skip encryption on a legacy system?
You must document a formal risk analysis showing compensating safeguards (e.g., network segmentation, strict RBAC, continuous monitoring) and sign an executive attestation. Keep evidence ready for auditors and update it annually or when the threat landscape changes.
How much budget should I allocate for key management and HSMs?
For mid-market healthcare orgs, plan on 15–20% of total security spend: 5–7% for HSM/KMS fees, 8–10% for personnel (crypto ops, audits), and 2–3% for tooling (monitoring, SIEM integrations). Outsourcing can trim CapEx but rarely eliminates OpEx.
How fast do I need to report a lost, unencrypted laptop with PHI?
HIPAA’s Breach Notification Rule requires notification “without unreasonable delay” and no later than 60 days after discovery. Most CISOs target 24 hours for executive notice and 48 hours for HHS/legal prep to stay well inside the limit.







